I doubt this was one of the persona scenarios envisioned for Mort, but apparently Mort has been busy writing a computer virus using Visual Basic (some would argue many VB programs are really viruses, but I digress; I've written plenty VB code myself!).
This virus reinforces that the biggest security risk is often from the inside!
jk
May 15, 2006
April 24, 2006
Microsoft password checker - misinformation
The blog entry at http://isc.sans.org/diary.php?storyid=1285 has some bad information that needs to be corrected regarding Microsoft's recently published password strength checker.
In this blog post, the autor states:
This is clearly NOT a Java applet if you take a cursory peek the HTML source! The password input button named 'pc001' has an event handler named 'onKeyUp' which calls a JavaScript method named EvalPwdStrength. This method is downloaded from here.
I notified SANS of the misinformation and requested a correction be published. I guess this is a good reminder that you can't believe everything you read on the internet; even from a popular site such as SANS (including my blog too!) :)
I agree with the SANS author's assertion that typing your passwords into a web page, no matter where it's hosted, is a bad idea. Just follow the guidelines and you'll have strong passwords.
If you have trouble remembering lots of strong passwords, try using a password manager program such as:
cheers
jk
In this blog post, the autor states:
GOOD it's a java applet that appears to run locally so your password is never sent over the internet
This is clearly NOT a Java applet if you take a cursory peek the HTML source! The password input button named 'pc001' has an event handler named 'onKeyUp' which calls a JavaScript method named EvalPwdStrength. This method is downloaded from here.
I notified SANS of the misinformation and requested a correction be published. I guess this is a good reminder that you can't believe everything you read on the internet; even from a popular site such as SANS (including my blog too!) :)
I agree with the SANS author's assertion that typing your passwords into a web page, no matter where it's hosted, is a bad idea. Just follow the guidelines and you'll have strong passwords.
If you have trouble remembering lots of strong passwords, try using a password manager program such as:
- >Password Minder by Keith Brown of Pluralsight
- >Password Safe by Bruce Schneier of Counterpane
cheers
jk
April 20, 2006
The lamest phishing attempt I've seen yet
I recieved an email today that apparently was some kind of phishing attempt. Yes, the "=20" were acutally part of the message.... :)
jk
Dear Customer,
Your current login & password = combination are=20 out of date.
To renew please click Reply and get back to us with the=20 following information:
Your Name, Account Number, Login and=20 Password.
Regards,
National City=20 Support
jk
April 19, 2006
banner ads are getting very specific
April 17, 2006
Some nice "running as non-admin" links
I was having trouble editing the power settings on my work laptop (running as non Administrator, non Power User).
So, firing up my trusy browser and favorite search engine resulted in a lot of nice links that I wanted to share.
Managing Power Options as a non-administrator
Temporary admin for your limited user account
Changing the system date, time and/or time zone (I feel less strongly about this one, but posted in case it was helpful)
and of course the granddaddy of posts:
Item 9: How to develop code as a non admin
Doing this requires some learning and some dicipline. There is a registry hack if you want to get Flash to work properly (i'll post that link sometime when i find it again).
jk
Edit 4/18/2006 12:56pm:
oops, forgot another granddaddy: Mr. Howard's Non-admin best practices in Windows XP
apologies to Mr. Howard :)
jk
So, firing up my trusy browser and favorite search engine resulted in a lot of nice links that I wanted to share.
Managing Power Options as a non-administrator
Temporary admin for your limited user account
Changing the system date, time and/or time zone (I feel less strongly about this one, but posted in case it was helpful)
and of course the granddaddy of posts:
Item 9: How to develop code as a non admin
Doing this requires some learning and some dicipline. There is a registry hack if you want to get Flash to work properly (i'll post that link sometime when i find it again).
jk
Edit 4/18/2006 12:56pm:
oops, forgot another granddaddy: Mr. Howard's Non-admin best practices in Windows XP
apologies to Mr. Howard :)
jk
April 15, 2006
Paypal Phishing Phake toolbar
yes, i know Phake is not a word. :)
Seriously, I see the phishing artists are hard at work with new ideas to trick people.
Tonight I received an email in my Junk Mail from "PayPal" which was clearly a phake. This is not new, we've all received emails like this.
I always like to open the phake link to see how accurate it looks compared to the real site. The interesting thing to note about this phishing site is they hid the real address bar and put in a simulated address bar textbox (the dropdown even sort of works on it).
In the picture below, the toolbar on the top with the address "http://0xd35bda31" is the 'real' toolbar (I right clicked and re-displayed the toolbar) and the toolbar with the "https://www.paypal.com/cgi-bin/webscr?cmd=_login-run" is the phake toolbar.
Is having a removable toolbar in IE really worth it? (I don't have FireFox installed, so I can't test it to see what it does on there. Maybe one of my loyal readers could do that and comment?). Web sites have long been able to hide/show the address and menu bars. Should my browser really allow some random website to voliate my boundries like this? One way to remedy this would be for browsers to create an option to override the ability for script to hide/show menu and address bars.
These types of phishing pages will only get more sophisticated and confusing. Please IE/FireFox, help protect users from this type of deception!
Here is the phake phishing link (PLEASE DON'T GIVE THEM ANY USEFUL INFO!)
Here is the screenshot of the browser with the phake toolbar:

I hope phishing is not good!
cheers
jk
Seriously, I see the phishing artists are hard at work with new ideas to trick people.
Tonight I received an email in my Junk Mail from "PayPal" which was clearly a phake. This is not new, we've all received emails like this.
I always like to open the phake link to see how accurate it looks compared to the real site. The interesting thing to note about this phishing site is they hid the real address bar and put in a simulated address bar textbox (the dropdown even sort of works on it).
In the picture below, the toolbar on the top with the address "http://0xd35bda31" is the 'real' toolbar (I right clicked and re-displayed the toolbar) and the toolbar with the "https://www.paypal.com/cgi-bin/webscr?cmd=_login-run" is the phake toolbar.
Is having a removable toolbar in IE really worth it? (I don't have FireFox installed, so I can't test it to see what it does on there. Maybe one of my loyal readers could do that and comment?). Web sites have long been able to hide/show the address and menu bars. Should my browser really allow some random website to voliate my boundries like this? One way to remedy this would be for browsers to create an option to override the ability for script to hide/show menu and address bars.
These types of phishing pages will only get more sophisticated and confusing. Please IE/FireFox, help protect users from this type of deception!
Here is the phake phishing link (PLEASE DON'T GIVE THEM ANY USEFUL INFO!)
Here is the screenshot of the browser with the phake toolbar:

I hope phishing is not good!
cheers
jk
April 14, 2006
A new kind of pop-up (meta-popup?)
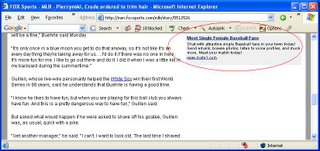
I was poking around Monster.com tonight and ran across the link to post jobs on.
Of course, there is a popup which my trusty Google toolbar popup blocker stops, but then I get this window...
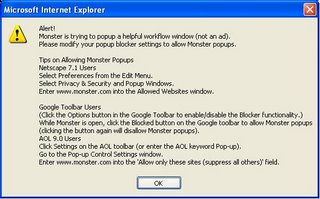
Yeah, like I'm planning on 'unblocking' popup windows...no matter how nicely they ask!
jk
Of course, there is a popup which my trusty Google toolbar popup blocker stops, but then I get this window...

Yeah, like I'm planning on 'unblocking' popup windows...no matter how nicely they ask!
jk
April 07, 2006
April 04, 2006
Improving credential collection, one site at a time
I recently opened a savings account at ING Direct. I was impressed with the login screen.
The first time I hit the page, it asked for:
The second time I hit the page (F5 - refresh), it asked for:
After a few more refreshes, it asked for:
True, if you know my customer number, birthday and SSN i'm still pretty much out of luck, but at least the pin transposition along with the different credentials combinations could help slow down an automated attack vector!
All that plus a better rate on my savings account! :)
cheers
jk
The first time I hit the page, it asked for:
- Customer number
- First 5 digits of my mailing zip code
- And my pin, transcribed visually into letters (see the picture, it is worth 1000 words!)
The second time I hit the page (F5 - refresh), it asked for:
- Customer number
- 4 year digit of my birth date
- And my pin, transcribed visually into letters, but using a different set of letters corresponding to each number (again, see the picture!)
After a few more refreshes, it asked for:
- First 4 digits of SSN
- Last 4 digits of SSN
- First 3 digits of SSN
- Last 3 digits of SSN
True, if you know my customer number, birthday and SSN i'm still pretty much out of luck, but at least the pin transposition along with the different credentials combinations could help slow down an automated attack vector!
All that plus a better rate on my savings account! :)
cheers
jk
Subscribe to:
Posts (Atom)